Block USB
One Click to block USB devices completely
Block External Devices
Easily block DVDs, iPods, external harddrive and etc from being accessed on your computers.
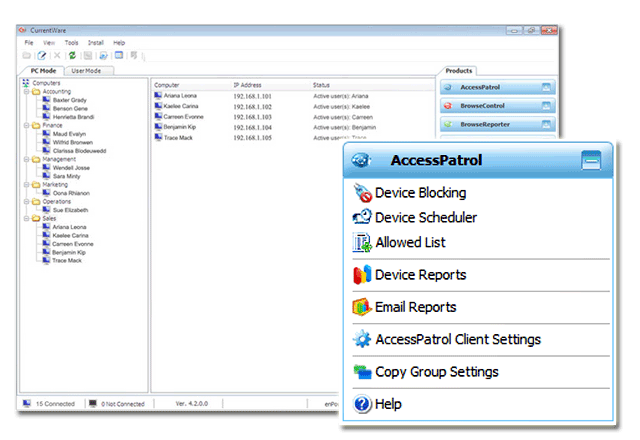
Device Permissions
Set full access, read only or no access on storage devices
Allowed List
Allow specific storage device to be always allowed on your network
Device Report
Report on devices accessed or blocked
Log USB File Transfer
Prevent data theft by monitoring files created and deleted on USB devices.
Access Code Generator
Provide end users with temporarily access to their endpoints
Email Alerts
Alert administrators of unauthorized file transfers and devices access.
Email Reports
Email device reports directly to your administrator's inbox.
Block Phones
Prevent users to plug their phones into the company's computer.
Devices Scheduler
Schedule device restrictions at specific time of the day
Stealth Mode
The CurrentWare client is running in the background in stealth mode
Centralized Console
Manage all your users and computers from a centralized Console
Remote Client Install
Easily deploy the CurrentWare Client remotely
Offsite Management
Keep device access policy enforced even when laptop is outside the network
SQL Server Supported
Database scaled for enterprise and large business operations






 Companies around the world are falling victim to data breaches and malware attacks because they are not implementing endpoint security software to protect their computers.
Companies around the world are falling victim to data breaches and malware attacks because they are not implementing endpoint security software to protect their computers.