Expect More, Pay Less!
Automate the
monitoring process for resource-constrained security pros with SureLog
software.
Security pros
can’t stop what they can’t see. But without the people to actively
monitor security activity, visibility is limited. SureLog was
specifically designed to address the monitoring needs of small security
staffs. SureLog delivers increased security visibility and reduced
time-to-respond duration without needing additional headcount.

Hundreds of supported data
sources plus embedded file integrity monitoring delivers rich
information for intelligent monitoring
Over 700 expert-developed
rules churn through data in real-time to pinpoint potential security
incidents
Active response can be
configured to automatically quarantine, block, or temporarily disable
suspicious activity

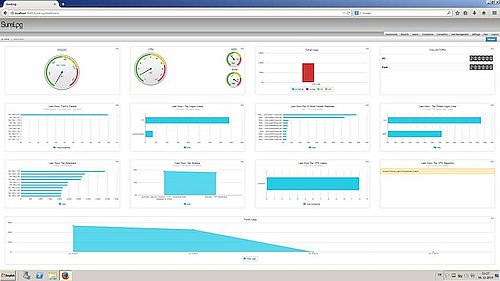
Intuitive dashboards for event
and log analysis plus rapid search enable security pros to quickly
assess incidents

Built-in intelligence across
networks, applications, and security speeds up root cause analysis
Simplify IT Compliance and
Regulatory Audit with SureLog
SureLog enables you to
effectively manage the impact of compliance risk on your organization.
Clients can track regulatory change, manage associated policies and
controls.
An effective monitoring
program implemented with SureLog addresses compliance gaps, demonstrates
risk management, and automates compliance reporting
Compliance
audits are quickly evolving from checklist-based to risk-based. To
address this increased scrutiny, organizations must demonstrate a strong
security focus while at the same time address time-consuming compliance
reporting requirements. SureLog helps regulated organizations get the
reporting automation they need while providing an all-in-one event and
log monitoring, investigation, and incident-response system that
supports risk-based monitoring.

Manage the
Cost of Security Operations while Improving Effectiveness
Whether you already have a SIEM that is
consuming your budget and resources or you are drowning in manual,
ineffective security processes, SureLog delivers solid ROI through
affordability, automation, and improved security.
It’s no secret that many SIEM
implementations are considered money pits. High license costs, overall
complexity, and the need for constant care and feeding have made many
organizations who desperately need SIEM benefits give up on it as a
solution. SureLog drastically reduces the costs of SIEM while providing
greater value to resource-constrained security pros. By eliminating the
development of large enterprise features that are seldom used and
focusing on those that improve operations, SureLog is offered at a very
affordable license, maintenance, and operational cost.
-
All-in-one
simple licensing model —licensing is typically less
than enterprise SIEM maintenance costs
-
Includes
traditional SIEM capabilities plus embedded log management, file
integrity monitoring, active response, policy-based USB blocking, and
SQL database monitoring
-
Our focus on
usability and deployment means no additional consulting, training, or
headcount required
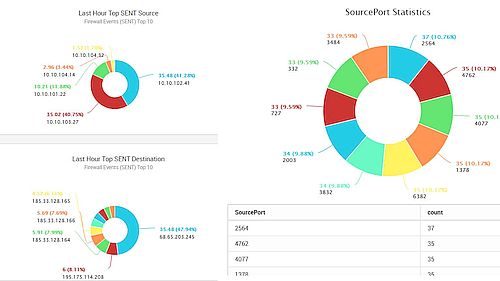
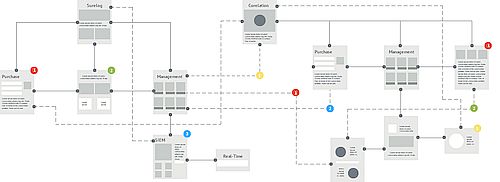
In-Memory Event Correlation
Access to true real-time log and event
correlation by processing log data before it is written to the database,
enabling you to immediately respond to security threats and vital
network issues with SureLog event correlation feature.
.jpg)
Event correlation is key to an effective
SIEM solution. But, not all correlation engines are built equally. With
SureLog, you get true, real-time in-memory event correlation to
instantly detect and mitigate threats. SureLog is a log analysis tool
which provides immediate incident awareness and actionable intelligence
so you can respond to vital issues at network speed.
SureLog’s real-time analysis means you’re
able to instantly take action to contain a threat or thwart an attack.
Moreover, SureLog provides automated, active responses for hands-free
threat mitigation, so you can safeguard your network 24x7.
SureLog enables you to effectively
troubleshoot both security and operational issues—be it a data breach or
a network performance problem—by understanding the relationship between
different activities using multiple event correlations. For instance, an
unauthorized application gets installed then a significant increase in
FTP traffic is seen going in and out of that system.
SureLog also has the unique ability to
set independent thresholds for activity per event, or group of events.
By combining SureLog’s powerful correlation and thresholding abilities,
you get security intelligence you can count on and reduce false
positives.
And, with over 300 built-in event
correlation rules and easy-to-understand categorization, SureLog
delivers visibility and control right out of the box. Correlation’s
library of configurable pre-built rules, along with the ability to
create advanced rules with easy rule editor, means you can say goodbye
to writing complex scripts to correlate events—eliminating hours of work
for you.
Get the Fastest EPS Performance
on the Market
A security information and event
management application is only as good as the amount of information it
can process in real-time. SureLog gives you the fastest events per
second (EPS) logging available today, so you can identify threats as
they occur.
Fast EPS performance is also critical to
maintaining compliance with ISO 9002 standards as well as SOX, HIPAA,
PCI and other federal regulations for online security. Your data will
stay safe, you'll be protected from liability, and you'll be ready for
surprise audits whenever they occur.