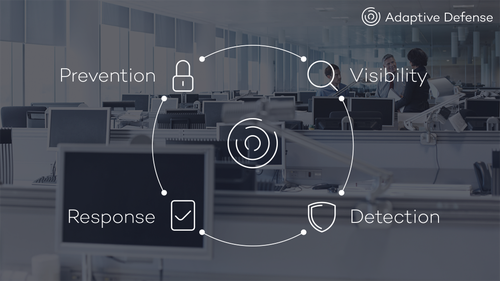
BLOCKING AND DISINFECTION:
This is the first and only advanced protection to combine disinfection and remediation capabilities.
Adaptive Defense 360 blocks and disinfects all malware detected.
CLASSIFICATION OF 100% OF RUNNING PROCESSES:
All active processes are classified, thereby guaranteeing protection against known malware and advanced attacks.
WE SEE WHAT OTHERS DON’T SEE:
Thanks to the classification of 100% of running processes, we are able to detect malware and anomalous behavior which other solutions can’t detect.
VISUAL AND DYNAMIC DATA FLOW:
See what is happening with each process and file. You will have a graphic, detailed analysis of the data flow represented on a dynamic map so you can see how and where malware has tried to enter, the action it tried to take, or who is trying to steal data and how.
DATA LEAKAGE DETECTION (DLD):
Prevent data leakage, whether perpetrated by malware or by employees copying data to physical drives or uploading it to the cloud.
CONTROL OVER VULNERABLE AND UNWANTED SOFTWARE:
Identify and resolve system and program vulnerabilities and prevent use of unwanted software (browser toolbars, adware, add-ons, etc.).
ADVANCED REPORTING TOOL:
Track security events through monitoring, data aggregation and correlation, notifications and real-time reports.
A HIGHLY AUTOMATED SOLUTION:
The combination of a managed service with a highly intuitive console and a light and simple agent reduces the workload of local IT staff to a minimum, and the impact on endpoints is negligible.