|
Features
Full Disk Encryption
Automatically encrypts all information on the hard
drive—including user data, the operating system,
temporary files and erased files, for maximum data
protection. Logical partitions are boot-protected and
encrypted sector-by-sector. Attempts to copy individual
files or to introduce rogue programs are blocked, even
when the hard drive is removed and slaved to a different
computer.
Pre-Boot
Authentication
Ensures that only
authorized users are allowed to access the
endpoint. All valid credentials must be provided
before the operating system will boot.
Multi-factor authentication options, such as
certificate-based Smartcards and dynamic tokens,
are supported. Multiple pre-boot authentication
languages are supported for global deployments.
Single-console, Intuitive User Interface
The Full Disk
Encryption Endpoint Software Blade provides an
intuitive user interface for centralized
management and easy viewing of security status
and log files or making basic configuration
changes.
Multiple client languages are for supported
for global deployments.
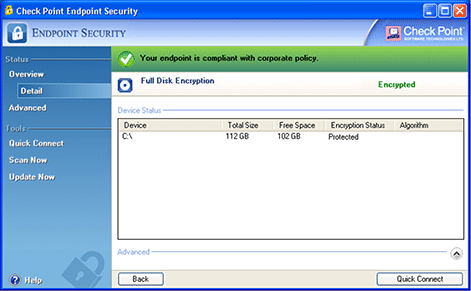
Centralized management with single console Secure Remote Help
Remote Password Change and One-Time Login remote
help options are available for users who may
have forgotten their passwords or lost access
tokens. Web-based remote help options are
available.
Central Management
The Full Disk Encryption Software Blade is
centrally managed by the
Endpoint Policy Management Software Blade,
enabling central policy administration,
enforcement and logging from a single,
user-friendly console. Centralized management
offers unmatched leverage and control of
security policies and multiple deployment
options offer easy installation and minimize
user impact, for a reduced overall cost of
operations.
Integrated into Check Point Software Blade
Architecture
The Full Disk Encryption Software Blade is
integrated into the Software Blade Architecture.
Endpoint Security Software Blades from Check
Point bring unprecedented flexibility, control
and efficiency to the management and deployment
of endpoint security. Choose from six Software
Blades to deploy only the protection you need,
with the freedom to increase security at any
time from a single central management console.
| 








